AppCheck is pleased to announce official support for integration into Microsoft’s Azure Pipelines. In this post we perform a brief review of Azure Pipelines, before looking at how you can leverage an AppCheck integration to deliver cheaper and faster security coverage, at lower cost and with greater assurance.
Microsoft’s Azure Devops is linked tool-chain of technologies and services that leverage DevOps ideas and techniques to deliver efficient utilisation of its cloud hosting platform, Azure, in a way that provides continuous delivery/integration (CI/CD) and ensures higher overall software quality at lower cost. Azure Pipelines offer a simple way for teams to build repeatable and automated workflows integrating build, test, package and release steps in a neatly visualised and centrally managed cloud tool-chain.
Security can often be divorced from software development – the responsibility of a separate team who simply “check” deployed artefacts via late-stage quality-gates such as penetration tests on deployed web applications. The problems with this approach are considerable: culturally, such split-brain concerns lead to friction, frustration and delays. A recent IBM study found that incorporating testing for security issues during implementation – rather than as a latest stage quality gate – could be 15 times cheaper. Focus has unsurprisingly shifted to the adoption of ’shift-left’ security strategies, whereby security testing is conducted earlier within the SDLC. In its most simple terms, “shift left” security is moving security to the earliest possible point in the development process.
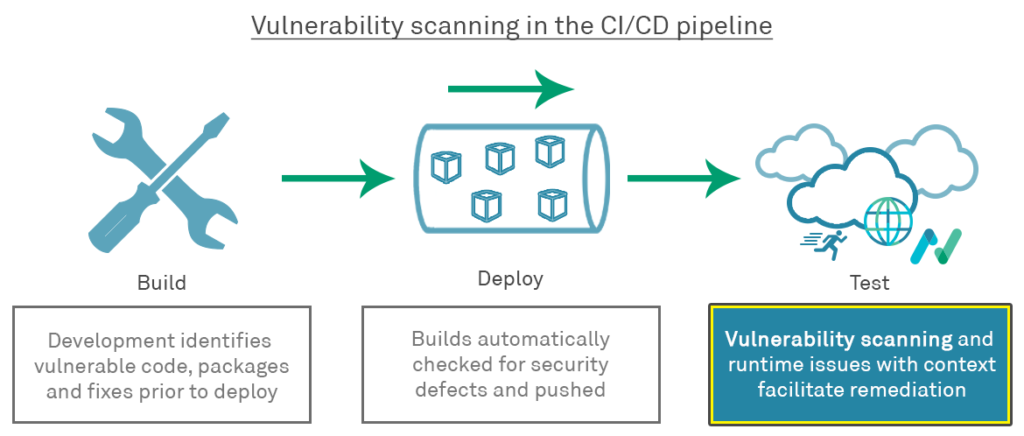
So if you already perform vulnerability scanning, what are the benefits to your team or organisation in integrating AppCheck into your Azure Pipelines?
Continuous Assurance
Penetration testing a deployed artefact or application provides a “one-off” assurance that the application is secure at a given point-in-time. However if your development team is using an agile or DevOps practices and your security team is not then there is an “assurance gulf” – a team deploying multiple times a day will swiftly move the application into a state whereby production code has been altered from “known good” state and assurance is lost. By comparison, vulnerability scanning via your Pipelines can be continuous and automated and repeated as often as every code deploy, providing ongoing assurance.
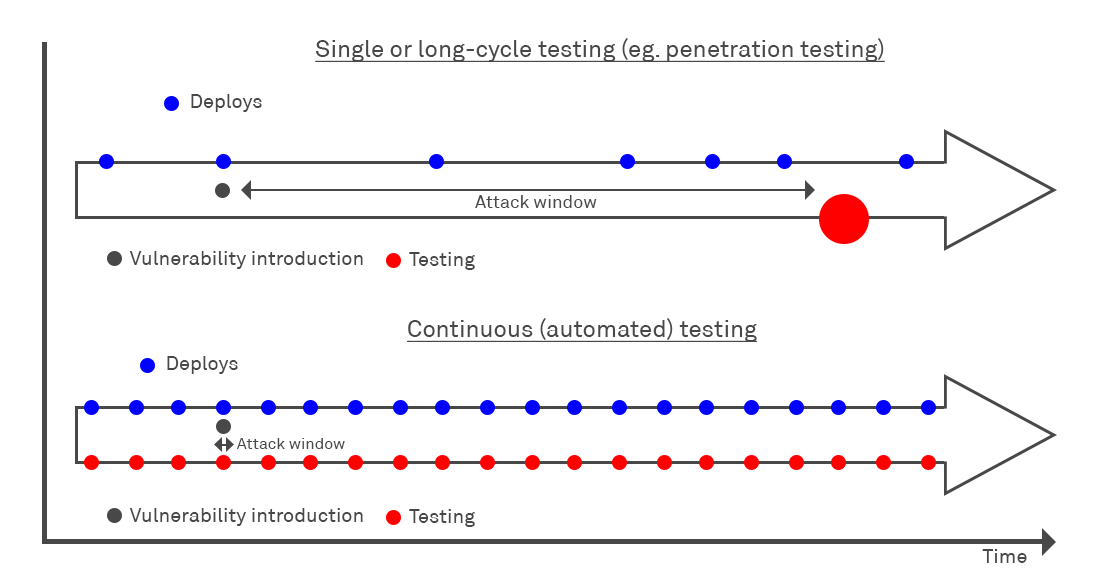
Shorter attack window
In security the “attack window” is an important concept representing the time gap that exists between introduction or creation of a vulnerability and its discovery and fix. If you rely solely on annual penetration tests, a vulnerability could exist on your deployed application for up to a year before being detected and sent for remediation. This creates a massively extended attack window that represents a significant opportunity for attackers to exploit your organisation.
Integrating security checks into your Pipeline, and scanning pre-deployment instances such as test and staging environments means that you can essentially reduce exploit availability to zero, patching all vulnerabilities prior to production release.
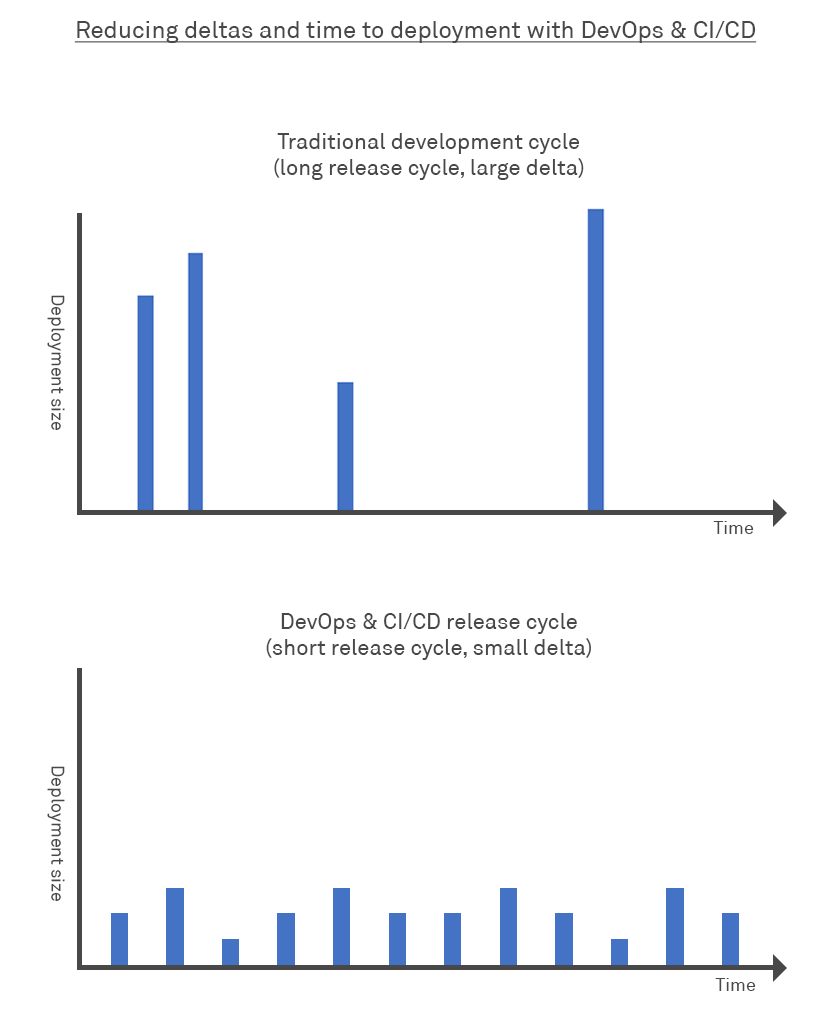
Quicker Fix
More regular vulnerability scan execution leads to the earlier detection of vulnerabilities and the need to consider or evaluate a far smaller change set for the source of the vulnerability, making it quicker and easier for the development team to identify the source of the vulnerability introduction from a smaller code delta, and make a smaller, more atomic fix in shorter timescale.
Deliver on Expectations
Quicker “fix as you go” leads to less late-stage delays and greater project delivery predictability – no more last minute blocks as the project hits late-stage security gates “wall” such as penetration tests and being delayed.
As with any new technology, there’s potential pitfalls that can prevent you reaping all the benefits that are on offer. We’ve put together a short selection of how you can ensure that you get the greatest value and lowest resistance in introducing DAST vulnerability scanning to your Azure Pipeline:
Start Small & Establish Success
Use the same agile methodology that you would elsewhere and start small. Pick one project, and trial your implementation on that, seeing what works and what doesn’t, and taking your lessons learned to apply to a wider trial and widespread adoption.
Collaborate
Ensure that you collaborate with and involve all relevant stakeholders from an early stage, gaining their input, ideas and energy. Share early trials with them for feedback and involve them from the inside so that they support and enable your initiative.
Risk Driven
AppCheck classifies vulnerabilities by severity of impact and probability of occurrence. You can leverage this to adopt a risk-driven approach, initially covering checks for your highest risk projects or code, and looking to identify only high-risk and critical findings, to ensure that your efforts are targeted where they add most value.
Maintain Velocity & Do Not Block
Integrate AppCheck into your Azure Pipelines in a “non blocking” report-only mode initially, so that you can gain input from the findings without causing frustration and delays to deployment. Remember that you are gaining insight where you had none initially, and there is no increased risk to your organisation by not “failing” builds based on detected vulnerabilities.
Metrics
Its an old DevOps maxim to “measure all the things”. If you can, gather metrics on everything, even if you don’t know why or how the data might be of use yet – how many vulnerabilities are found in each codebase? How many times are you running scans? How long are scans taking to run? All these metrics can help provide answers further down the road and you’ll appreciate the data being there when you need it.
No Blame
Remember that detecting vulnerabilities further left is about reducing the cost of remediation, and development teams must be keen to leverage the solution rather than afraid to do so. Its important therefore not to culturally punish teams for reporting vulnerabilities in their code, but rather recognising that vulnerabilities will always exist, and a team finding bugs may simply be leveraging the vulnerability scanning solution more maturely and effectively.
Get in contact with us today to find out more: info@localhost
See our Azure Pipeline Integration Guide here
Get the AppCheck Azure Pipeline plug-in now
[Please note to make use of this plug-in you will require an additional licence key. Please enquire for costs.]
AppCheck help you with providing assurance in your entire organisation’s security footprint. AppCheck performs comprehensive checks for a massive range of web application vulnerabilities from first principle to detect vulnerabilities in in-house application code. AppCheck also draws on checks for known infrastructure vulnerabilities in vendor devices and code from a large database of known and published CVEs. The AppCheck Vulnerability Analysis Engine provides detailed rationale behind each finding including a custom narrative to explain the detection methodology, verbose technical detail and proof of concept evidence through safe exploitation.
As always, if you require any more information on this topic or want to see what unexpected vulnerabilities AppCheck can pick up in your website and applications then please get in contact with us: info@localhost
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







