Cisco, best known for its networking hardware and software lines, typically releases security advisories on a weekly basis. These advisories contain details of new vulnerabilities as well as instructions for obtaining product security updates. In this blog post, we summarise key details for all Cisco security fixes released in the last month, as well as highlight some of the most critical issues. The full list of advisories can be viewed in full via the Cisco Security Center website, at: https://sec.cloudapps.cisco.com/security/center/publicationListing.x.
We reported in our weekly ‘KEV’ roundup earlier this month that attackers have been hacking Cisco Devices by Creating Arbitrary Admin Accounts On-Demand CVE-2023-20198. That exploitation involves a critical flaw in the web admin UI of Cisco devices that run the firm’s proprietary IOS XE – including Catalyst switches and routers. Already exploited at scale as a ‘0-day’ back in 2023, the vulnerability is now seeing exploitation all over again.
In a separate weekly ‘KEV’ roundup, we also highlighted the active exploitation of a missing authentication check in the web management interfaces of Cisco’s RV series routers CVE-2019-1653. Originally flagged by CISA in November 2021, this vulnerability has been actively exploited by the threat actor ‘Volt Typhoon’. The renewed attention follows a report by NST Cyber, which listed it amongst the ‘Top 10 Most Exploited CVEs Against Enterprise Applications’ for the week of February 12th 2025.
Finally, researchers from Cisco’s Talos group report a second wave of activity exploiting Cisco’s Smart Install Feature in both IOS and IOS XE CVE-2018-0171. The latest wave of attacks have been attributed to the APT group known as ‘Salt Typhoon’, as part of its campaign to deploy the ‘JumbledPath’ malware. Targets are said to have included government entities and telecommunication companies.
The Cisco security advisories issued in February 2025 also include high-priority fixes for two critical flaws in Cisco’s Identity Services Engine (ISE) – exploit could allow an authenticated, remote attacker to execute arbitrary commands and elevate privileges on an affected device. There are several further ‘High’ priority fixes for vulnerabilities in the company’s IOS, IOS XE, IOS XR and NX-OS Software.
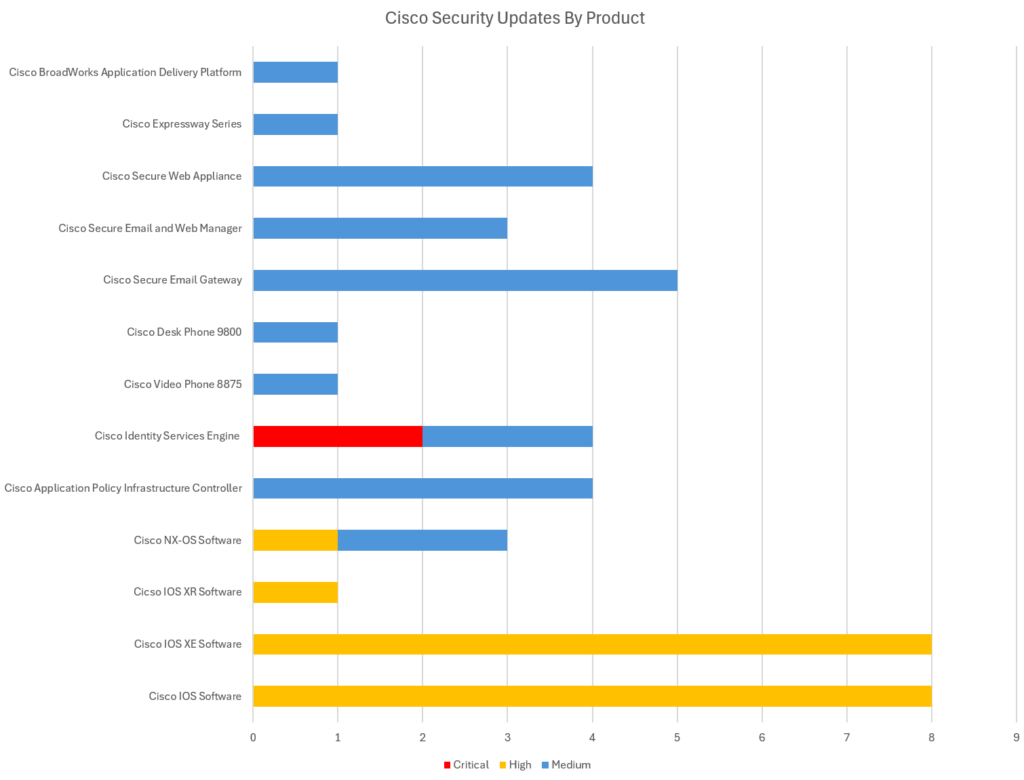
The list of ‘Critical’ severity vulnerabilities below are those that Cisco have rated as 9.0 or higher out of 10 under the “CVSS” (Common Vulnerability) scoring system – although this is at the discretion of Cisco. These vulnerabilities typically represent a critical risk to organisations – being both trivial for attackers to exploit, as well as having the potential to have significant impact (harm) if successfully exploited. Critical vulnerabilities are crucial to patch, and remediation is time sensitive – these types of vulnerabilities often feature in our “Known Exploited Vulnerabilities” (KEV) roundups as undergoing active exploitation if a threat group develops working exploit code and begins to actively target organisations. The vulnerabilities flagged as Critical severity in Cisco products this month includes:
| Cisco Product | CVE ID | CVSS Score |
|---|---|---|
| Cisco Identity Services Engine (ISE) – Java Deserialization Vulnerability | CVE-2025-20124 | 9.9 |
| Cisco Identity Services Engine (ISE) – Authorization Bypass Vulnerability | CVE-2025-20125 | 9.1 |
The list of ‘high’ severity vulnerabilities below are those that Cisco have rated between 7.0 and 8.9 out of 10 under the “CVSS” (Common Vulnerability) scoring system. High-severity vulnerabilities are still important to prioritise for remediation, but they are rated as a slightly lower risk than ‘critical’ vulnerabilities. This may be because they are either harder for attackers to exploit (such as requiring local rather than network access to exploit) or else considered to have a typically lower impact on systems and services if they were to be exploited. The vulnerabilities regarded as ‘High’ in Cisco products this month include:
| Cisco Product | CVE ID | CVSS Score |
|---|---|---|
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20169 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20170 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20171 | 7.7 |
| Cisco IOS, IOS XE, and IOS XR Software – Denial of (DoS) Service Vulnerability | CVE-2025-20172 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20173 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20174 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20175 | 7.7 |
| Cisco IOS and IOS XE Software – Denial of Service (DoS) Vulnerability | CVE-2025-20176 | 7.7 |
| Cisco NX-OS Software – Denial of Service (DoS) Vulnerability | CVE-2025-20111 | 7.4 |
All our vulnerability entries above contain links to official remediation guidance from Cisco in the form of their published Security Advisories, as well as details of mitigations or workarounds that can be performed if immediate patching is not possible. Cisco release free software updates and customers within service contracts are entitles to regular software updates containing security fixes via update channels.
To help customers determine their exposure to vulnerabilities in Cisco ASA, FMC, and FTD Software, Cisco also provides the Cisco Software Checker tool, available at https://sec.cloudapps.cisco.com/security/center/softwarechecker.x, which can be used to check if a specific software release is vulnerable to a given vulnerability.
We also recommend scanning your entire estate using the AppCheck vulnerability scanner regularly – both server systems and networking infrastructure, as well as end-user machines running desktop operating systems – in order to detect known vulnerabilities in your technical estate. Contact your account manager now to enquire about license options for our ‘internal scan hubs’ solution or, if not already a customer, take our platform for a test drive today at https://appcheck-ng.com/.
The upcoming dates for the next four monthly Cisco roundups will be:
Add them to your calendar now!
Also keep an eye on our blog for coverage of other critical vulnerability updates including:
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







