“Patch Tuesday” is an unofficial term referring to the second Tuesday of each month, when vendors including Microsoft, Adobe, SAP and Google coordinate the release of vulnerabilities in (and patches for) their software products on a fixed cycle. Critical security updates are occasionally released outside of the normal Patch Tuesday cycle, but these are known as “out-of-band” releases.
In this blog post we’ll summarise the key Microsoft Security Updates for the month, but you can access the raw list in full directly at https://msrc.microsoft.com/update-guide/releaseNote/2024-Dec
Microsoft reported the successful exploitation of its low-code ‘Power Apps’ platform in late November (CVE-2024-49035). ‘Power Apps’ isn’t yet a household name in Microsoft’s portfolio – the product is Microsoft’s entry into the ‘low-code’ space, designed to compete against a wide range of offerings from Appian, AppSmith, SalesForce, Zoho and others. Details are extremely sparse – as is typical from the traditionally tight-lipped Microsoft – but the company has simply reported that the platform has “been exploited”.
Later this month, a server-side request forgery (SSRF) vulnerability in Microsoft’s Exchange Server from 2021 (CVE-2021-26855) was revealed to be one of a set of four vulnerabilities being leveraged in an exploit chain dubbed ‘ProxyLogin’ – the flaw has been listed as one of the “TOP 10 most exploited” vulnerabilities for the year in a report published this week by Cato Networks.
And finally, a vulnerability in Microsoft Windows dating back to 2023 (CVE-2023-32046) was recently discovered being exploited in the wild again. A suspected Russian threat actor identified as ‘UAC-0194’ has been observed distributing a zip archive containing files vulnerable to this flaw.
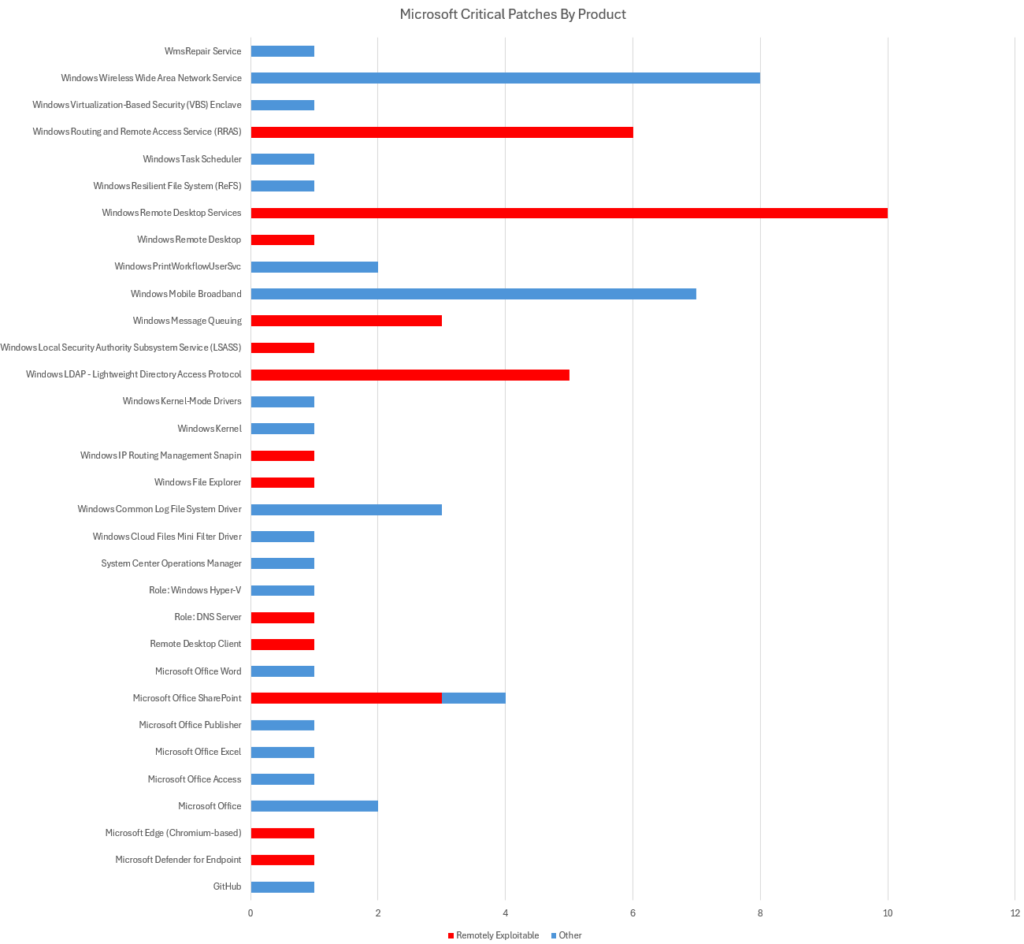
Patches for all three are available now. The Microsoft Patch Tuesday update for December 2024 also includes important updates for vulnerabilities in products including Microsoft Office, Microsoft Edge, Microsoft Defender, GitHub, Microsoft Word, Microsoft SharePoint, Microsoft Excel, System Center Operations Manager, Windows Mobile Broadband, Remote Desktop Client, WmsRepair Service and Microsoft Access.
The list of “Known Exploited” vulnerabilities below represent the greatest risk and absolute highest priority for patching for many organisations. They have been reported by the CISA, America’s Cyber Defense Agency, to be known to be currently being exploited in the wild and at scale, meaning that not only is exploit code known to attackers, but that the weakness is being actively targeted. These vulnerabilities are the most time-critical to patch before being exploited by threat actors.
The AppCheck Scanner is able to detect these vulnerabilities and report on their presence in your technical estate, enabling you to effectively and swiftly target them for remediation – please click each CVE below to read more about each entry on our public-facing Detections database.
| Product | CVE | CVSS Score |
|---|---|---|
| Microsoft Windows – Privilege Escalation via Heap-based Buffer Overflow in CLFS Driver | CVE-2024-49138 | 8.7 |
The list of “Critical” vulnerabilities below are all those with a “CVSS” (Common Vulnerability Scoring System) score of 9.0 or greater. This generally reflects a vulnerability that is a critical risk – being both trivial to exploit as well as having the potential to have significant impact (harm) if successfully exploited – but for which no hard evidence has been gathered yet as to ongoing exploitation. Critical vulnerabilities are crucial to patch, but may be slightly less time-sensitive than ‘known exploited’ vulnerabilities. Critical vulnerabilities highlighted by Microsoft this month include:
| Product | CVE | CVSS Score |
|---|---|---|
| Microsoft Windows – LDAP Remote Code Execution (RCE) Vulnerability | CVE-2024-49112 | 9.8 |
The list of “Highly Exploitable” vulnerabilities below are all those which Microsoft has determined are relatively trivial to exploit. Unlike the ‘known exploited vulnerabilities’ list above, there is no evidence yet released of these vulnerabilities having been exploited ‘in the wild’, but that could well change if exploit code is published, or a threat actor chooses to specifically target one of these vulnerabilities. The vulnerabilities flagged as ‘highly exploitable’ by Microsoft this month include:
| Product | CVE | CVSS Score |
|---|---|---|
| Microsoft SharePoint – Remote Code Execution (RCE) Vulnerability | CVE-2024-49070 | 7.4 |
| Microsoft Windows (CLFS Driver) – Elevation of Privilege Vulnerability | CVE-2024-49088 | 7.8 |
| Microsoft Windows (CLFS Driver) – Elevation of Privilege Vulnerability | CVE-2024-49090 | 7.8 |
| Microsoft Windows (ReFS) – Elevation of Privilege Vulnerability | CVE-2024-49093 | 8.8 |
| Microsoft Windows (CFMF Driver) – Elevation of Privilege Vulnerability | CVE-2024-49114 | 7.8 |
| Microsoft Message Queuing (MSMQ) – Remote Code Execution (RCE) Vulnerability | CVE-2024-49122 | 8.1 |
In addition to the above, Microsoft released 72 important security patches in total.
Products affected by this Patch Tuesday’s updates include:
Total Microsoft CVEs: 72
Known Actively Exploited: 1
Critical: 1
Highly Exploitable: 6
Other vendors releasing critical security updates this Patch Tuesday include:
As with every month, if you don’t want to wait for your system to download Microsoft critical updates on pre-determined schedule, you can download them immediately from the Windows Update Catalog website at https://www.catalog.update.microsoft.com/Home.aspx and searching by Microsoft KB ID.
We also recommend scanning your entire estate using the AppCheck vulnerability scanner regularly – including end-user machines running desktop operating systems. Contact your account manager now if you are not already licensed for internal scan hubs to cover your whole estate.
The next MICROSOFT Patch Tuesday update will be on 8th January 2025 – add it to your calendar now!
We also now provide coverage of other critical vulnerability updates from key vendors, including:
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







