“Patch Tuesday” is an unofficial term used to refer to the second Tuesday of each month, when Microsoft, Adobe, Oracle and others regularly release software patches for their software products. Critical security updates are occasionally released outside of the normal Patch Tuesday cycle, but these are known as “Out-of-band” releases.
You can access the Microsoft list of Security Updates for May 2024 directly at msrc.microsoft.com/update-guide/releaseNote/2024-May
The list of “Known Exploited” vulnerabilities below have been reported by the CISA, America’s Cyber Defense Agency, to be known to be currently being exploited in the wild and at scale. These represent the absolute highest priority for patching for many organisations:
The first key vulnerability to highlight this month is the ability of attackers to bypass the OLE Security and Protection Mechanisms in the MSHTML Platform of Microsoft Windows desktop and server operating systems (CVE-2024-30040) and gain arbitrary code execution, due to an input validation failure. This vulnerability has been reported as being actively exploited in the wild by threat groups and should be patched as a priority.
See full details of the above vulnerability online via our Detections Service at https://detections.appcheck-ng.com/vulnerabilities/view/294634.
AppCheck already is detecting and reporting on instances of this vulnerability, so ensure that you check your latest scan reports for potential threat to your estate.
A second vulnerability also in Microsoft Windows – CVE-2024-30051 – has also been reported as “exploitation detected” by Microsoft. A heap-based buffer overflow vulnerability in Windows DMM Core Library with a CVSS score of 7.8 (“high” risk), this vulnerability can be exploited to in both server and desktop editions of Windows to achieve privilege escalation to the privileged ‘SYSTEM’ context.
See full details of the above vulnerability online via our Detections Service at https://detections.appcheck-ng.com/vulnerabilities/view/294633.
AppCheck already is detecting and reporting on instances of this vulnerability, so ensure that you check your latest scan reports for potential threat to your estate.
The list of “Critical” vulnerabilities below are all those with a “CVSS” score of 9 or greater. This generally reflects a vulnerability that is critical risk, being both trivial to exploit, likely to be exploited, and which could cause great harm and damage if exploited:
None of the vulnerabilities reported so far this month as of Patch Tuesday have been rated as “critical” (CVSS 9+), although CVSS 8.8 vulnerabilities exist in services and products including: Microsoft Office SharePoint; Windows Hyper-V; Windows Routing and Remote Access Service (RRAS); Microsoft Brokering File System; and the Microsoft WDAC OLE DB provider for SQL.
The list of “Highly Exploitable” vulnerabilities below are all those which Microsoft has determined are relatively trivial to exploit:
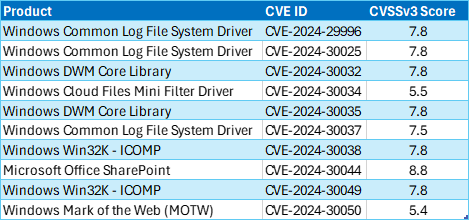
In addition to the above, Microsoft released 60 important security patches in total.
Products affected by this Patch Tuesday’s updates include:
You can see the full list on Microsoft’s Security Update Guide page (https://msrc.microsoft.com/update-guide/en-us), along with the associated KB articles and security vulnerability details.
Total Microsoft CVEs: 60
Currently exploited: 2
Highly Exploitable: 10
By Severity:
As with every month, if you don’t want to wait for your system to download Microsoft critical updates on pre-determined schedule, you can download them immediately from the Windows Update Catalog website at https://www.catalog.update.microsoft.com/Home.aspx and searching by Microsoft KB ID.
We also recommend scanning your entire estate using the AppCheck vulnerability scanner regularly – including end-user machines running desktop operating systems. Contact your account manager now if you are not already licensed for internal scan hubs to cover your end-user estate and find out how to delivery holistic, whole-estate coverage for your organisation.
The next Patch Tuesday will be on 11th June 2024 – add it to your calendar now!
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







