Oracle releases security fixes for supported on-premises (non-cloud) products as part its regular Critical Patch Updates (CPUs) cycle. The current release schedule for CPUs is on the third Tuesday of January, April, July, and October each year. Additional security fixes are occasionally released outside of the normal cycle, but these are known as “out-of-band” security alerts and bulletins.
Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply all applicable security patches found within the Critical Patch Updates as soon as possible.
In this blog post, we will be summarising key details for the security patches contained within the latest product updates. The raw list can be viewed in full directly here: https://www.oracle.com/security-alerts/cpujan2025.html. You can also access a list of historical CPUs here: https://www.oracle.com/security-alerts/.
The Oracle product ecosystem continues to pose a lucrative target for attackers, with the company reporting the confirmed exploitation this quarter of a critical access control bypass vulnerability in its Agile Product Lifecycle Management (PLM) Framework that led to the exfiltration of highly sensitive commercial data (CVE-2024-21287). Also exploited in the wild this quarter was a critical vulnerability in the company’s WebLogic Server (CVE-2020-2883), part of it Fusion Middleware platform.
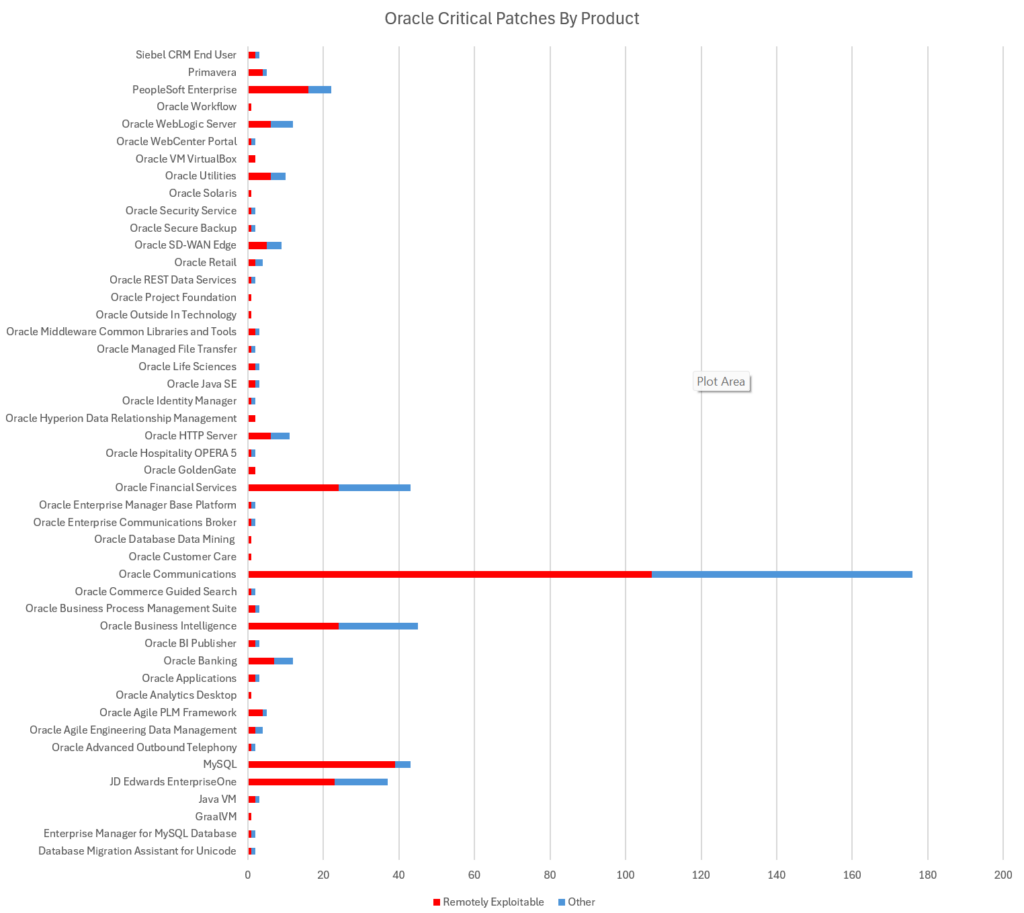
The Oracle Critical Patch Updates for November 2024 through January 2025 also includes important updates for vulnerabilities in other products including Oracle Financial Services, Oracle Communications, PeopleSoft, JDEdwards EnterpriseOne Tools, MySQL Enterprise Backup, Oracle BI Publisher, Oracle SD-WAN Edge and Oracle Agile Engineering Data Management.
The list of “Highly Exploitable” critical vulnerabilities below are those which have a ‘critical’ impact – rated as 9.0 or more out of 10 under the “CVSS” (Common Vulnerability) scoring system – but are also considered to be relatively trivial to exploit. They have (a) a network attack vector, (b) a low attack complexity, and (c) are remotely exploitable without authentication. This reflects those vulnerabilities that are believed to present the most critical risk to organisations, since they are both trivial to target, as well as having the potential to have significant impact (harm) if successfully exploited. “Highly exploitable” critical vulnerabilities are crucial to patch, and remediation is time sensitive – these type of vulnerabilities often feature in our “Known Exploited Vulnerabilities” (KEV) roundups as undergoing active exploitation if a threat group develops working exploit code and begins to actively target organisations. The vulnerabilities regarded as ‘highly exploitable’ criticals in Oracle products this month includes:
| Product | CVE | CVSS Score |
|---|---|---|
| Oracle Agile PLM Framework – Privilege Escalation Vulnerability in Agile Integration Services Component | CVE-2025-21556 | 9.9 |
| Oracle Communications Policy Management – Race Condition in Configuration Management Platform (Apache Tomcat) Component | CVE-2024-56337 | 9.8 |
| JD Edwards EnterpriseOne Tools – Access Control Bypass in Monitoring and Diagnostics SEC Component | CVE-2025-21524 | 9.8 |
| Oracle WebLogic Server – Authentication Bypass Vulnerability in Core Component | CVE-2025-21535 | 9.8 |
| Oracle BI Publisher – Deserialization Vulnerability in DevOps Spring Framework Component | CVE-2016-1000027 | 9.8 |
| Oracle Agile Engineering Data Management – ‘Use After Free’ in Core (Apache Xerces-C++) Component | CVE-2024-23807 | 9.8 |
| Oracle Business Intelligence Enterprise Edition – ‘Use After Free’ in Analytics Server (SciPy) Component | CVE-2023-29824 | 9.8 |
| JD Edwards EnterpriseOne Tools – Path Traversal in E1 Dev Platform Tech Cloud (Samba) Component | CVE-2023-3961 | 9.8 |
| Oracle Communications Diameter Signaling Router – Deserialisation Vulnerability in Patches (Apache ActiveMQ) Component | CVE-2023-46604 | 9.8 |
| Oracle Communications Network Analytics Data Director – Integer Overflow in Install/Upgrade (LibExpat) Component | CVE-2024-45492 | 9.8 |
| Oracle Financial Services Behavior Detection Platform – Integer Overflow in Platform (LibExpat) Component | CVE-2024-45492 | 9.8 |
| Oracle Financial Services Trade-Based Anti Money Laundering Enterprise Edition – Integer Overflow in LibExpat Component | CVE-2024-45492 | 9.8 |
| Oracle HTTP Server – Integer Overflow in Core (LibExpat) Component | CVE-2024-45492 | 9.8 |
| Oracle HTTP Server – Information Disclosure via Buffer Over-Read in Mod_Security (OpenSSL) Component | CVE-2024-5535 | 9.1 |
| Oracle Business Intelligence Enterprise Edition – Information Disclosure via Buffer Over-Read in OpenSSL Component | CVE-2024-5535 | 9.1 |
| PeopleSoft Enterprise PeopleTools – Information Disclosure via Buffer Over-Read in OpenSSL Component | CVE-2024-5535 | 9.1 |
| Oracle HTTP Server – Path Traversal Vulnerability in Mod_rewrite (Apache HTTP Server) Component | CVE-2024-38475 | 9.1 |
| Oracle Business Intelligence Enterprise Edition – XXE Vulnerability in BI Platform Security (Apache XMLBeans) Component | CVE-2021-23926 | 9.1 |
| MySQL Enterprise Backup – Credential Disclosure in Enterprise Backup (curl) Component | CVE-2024-11053 | 9.1 |
| MySQL Server – Credential Disclosure in Server Packaging (curl) Component | CVE-2024-11053 | 9.1 |
| Oracle Communications Billing and Revenue Management Platform – Out-of-Bounds Read in Kerberos Component | CVE-2024-37371 | 9.1 |
| Oracle Communications Diameter Signaling Router – Out-of-Bounds Read in Automated Test Suite (Kerberos) Component | CVE-2024-37371 | 9.1 |
| Oracle Communications User Data Repository – Out-of-Bounds Read in Platform (Kerberos) Component | CVE-2024-37371 | 9.1 |
| Oracle SD-WAN Edge – Out-of-Bounds Read in Internal tools (Kerberos) Component | CVE-2024-37371 | 9.1 |
| Oracle Security Service – Out-of-Bounds Read in Security Toolkit (Kerberos) Component | CVE-2024-37371 | 9.1 |
| MySQL Server – Out-of-Bounds Read in Server Packaging (Kerberos) Component | CVE-2024-37371 | 9.1 |
| Oracle Hospitality OPERA 5 – Denial of Service (DoS) Vulnerability in Opera Servlet Component | CVE-2025-21547 | 9.1 |
Although Oracle considers all 318 vulnerabilities in their update to be critical, the list of “Critical” vulnerabilities below are those that Oracle have assigned a CVSS score of 9.0 or more, the threshold for ‘critical’ risk under the CVSS scoring system. Unlike the ‘highly exploitable’ vulnerabilities listed above, these vulnerabilities may be slightly more difficult for attackers to leverage. They may, for instance, not be remotely exploitable, or may require authentication in order to access. Potential exploit is still possible, especially as part of an exploit chain of multiple vulnerabilities. However, although the risk remains extremely high, it is slightly lower than that of the “highly exploitable” vulnerabilities listed above. Additional critical vulnerabilities highlighted by Oracle this month include:
| Product | CVE | CVSS Score |
|---|---|---|
| Oracle Agile PLM Framework – Privilege Escalation Vulnerability in Agile Integration Services | CVE-2025-21556 | 9.9 |
| Oracle Communications Policy Management – Path Traversal Vulnerability in Configuration Management Platform (Apache Struts 2) | CVE-2024-53677 | 9.0 |
| Oracle Communications Cloud Native Core Console – RADIUS Protocol Vulnerability in Kerberos Component | CVE-2024-3596 | 9.0 |
| Oracle Communications Operations Monitor – RADIUS Protocol Vulnerability in Mediation Engine (pyrad) | CVE-2024-3596 | 9.0 |
Total Oracle CVEs: 318
Highly Exploitable Critical Vulnerabilities: 26
Total Critical Vulnerabilities: 30
We recommend scanning your entire estate using the AppCheck vulnerability scanner regularly – both server systems and networking infrastructure, as well as end-user machines running desktop operating systems. Contact your account manager now if you are not already licensed for ‘internal scan hubs’ to cover scanning of your entire technical estate.
The next four dates for Critical Patch Updates will be on:
Add them to your calendar now!
Also keep an eye on our blog for coverage of other critical vulnerability updates including:
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







