Palo Alto Networks offers a variety of products to help secure networks, including firewalls, endpoint protection, and cloud security. The company are perhaps best known for their Cortex, Prisma and PA-Series of Next Generation Firewalls (NGFW). Palo Alto typically releases security advisories on a monthly basis. These advisories contain details of new vulnerabilities as well as instructions for obtaining product security updates. In this blog post – part of a series published every month on the second Thursday of the month – we summarise key details for all Palo Alto security advisories released in the last month, as well as highlight some of the most critical issues that organisations should address. The full list of advisories can be viewed in their original format via the Palo Alto Networks Security Advisories, published at: https://security.paloaltonetworks.com/.
For Palo Alto, the last few weeks have seen something of a bumpy ride which started with CISA releasing an advisory regarding the ongoing active exploitation of a critical vulnerability in the company’s ‘Expedition’ migration software. As if this wasn’t bad enough, it was followed only days later when the company itself released its own advisory. In this case it had received information of a so-called ‘0-day’ (previously unknown, and no fix available) Remote Code Execution (RCE) vulnerability in its PAN-OS software that was potentially being exploited in the wild.
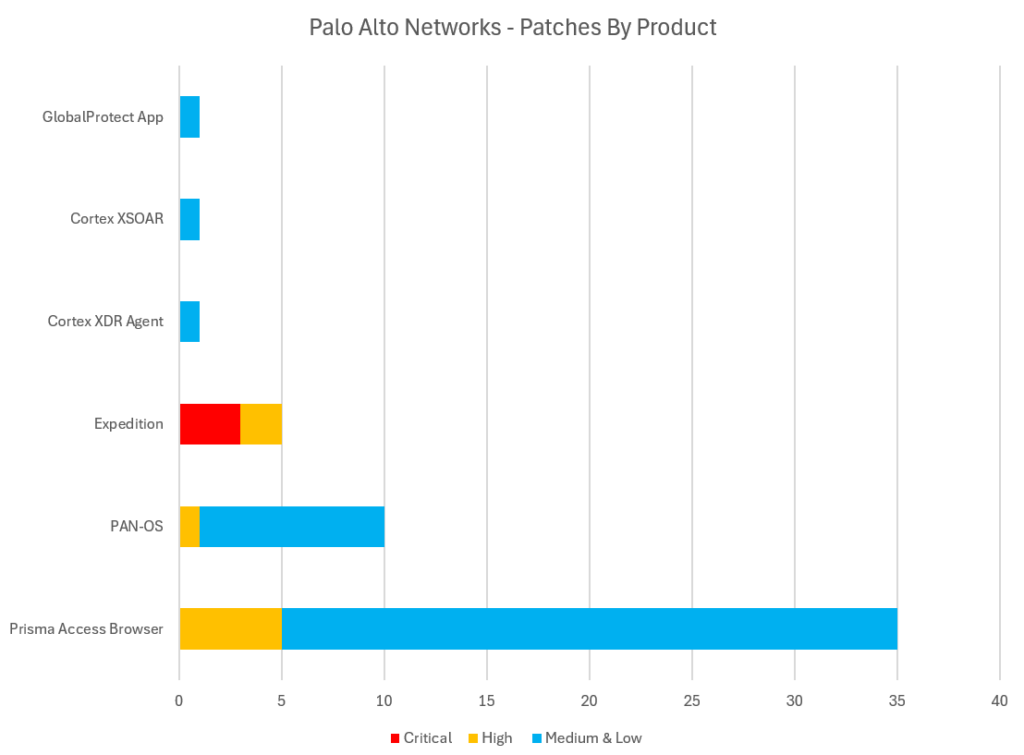
The Palo Alto security advisories issued in the four-week period ending 13th November 2024 include high-priority fixes for critical Authentication Bypass, Memory Management and Denial of Service (DoS) vulnerabilities in products including the company’s PAN-OS software and ‘Expedition’ migration software, as well as a slew of memory management flaws and input validation failures in its ‘Prisma’ Chromium-Based Browser.
Additional products receiving lower priority patches this month include the company’s GlobalProtect App, Cortex XSOAR and Cortex XDR Agent software.
The list of ‘Critical’ severity vulnerabilities below are those that Palo Alto have rated as 9.0 or higher out of 10 under the “CVSS” (Common Vulnerability) scoring system – although this is at the discretion of Palo Alto. These vulnerabilities typically represent a critical risk to organisations – being both trivial for attackers to exploit, as well as having the potential to have significant impact (harm) if successfully exploited. Critical vulnerabilities are crucial to patch, and remediation is time sensitive – these types of vulnerabilities often feature in our “Known Exploited Vulnerabilities” (KEV) roundups as undergoing active exploitation if a threat group develops working exploit code and begins to actively target organisations. The vulnerabilities flagged as Critical severity in Palo Alto Networks products this month includes:
| Palo Alto Networks Product | Palo Alto Reference | CVE IDs | CVSS Score |
|---|---|---|---|
| Palo Alto Expedition – OS Command Injection Vulnerability | PAN-SA-2024-0010 | CVE-2024-9463 | 9.9 |
| Palo Alto Expedition – OS Command Injection Vulnerability | PAN-SA-2024-0010 | CVE-2024-9464 | 9.3 |
| Palo Alto Expedition – SQL injection Vulnerability | PAN-SA-2024-0010 | CVE-2024-9465 | 9.2 |
The list of ‘High’ severity vulnerabilities below are those that Palo Alto have rated between 7.0 and 8.9 out of 10 under the “CVSS” (Common Vulnerability) scoring system. High-severity vulnerabilities are still important to prioritise for remediation, but they are rated as a slightly lower risk than ‘critical’ vulnerabilities. This may be because they are either harder for attackers to exploit (such as requiring local rather than network access to exploit) or else considered to have a typically lower impact on systems and services if they were to be exploited. The vulnerabilities regarded as ‘High’ in Palo Alto products in the last four weeks include:
| Palo Alto Networks Product | Palo Alto Reference | CVE ID | CVSS Score |
|---|---|---|---|
| Prisma Access Browser – Multiple Vulnerabilities | PAN-SA-2024-0011 | CVE-2024-8904 | 8.6 |
| PAN-OS – Firewall Denial of Service (DoS) Vulnerability | PAN-244840 | CVE-2024-9468 | 8.2 |
| Palo Alto Expedition – Cleartext Storage of Sensitive Data | PAN-SA-2024-0010 | CVE-2024-9466 | 8.2 |
| Palo Alto Expedition – Reflected XSS Vulnerability | PAN-SA-2024-0010 | CVE-2024-9467 | 7.0 |
| Prisma Access Browser – Implementation Error | PAN-SA-2024-0016 | CVE-2024-10229 | 8.1 |
| Prisma Access Browser – Type Confusion Vulnerability | PAN-SA-2024-0016 | CVE-2024-10230 | 8.8 |
| Prisma Access Browser – Type Confusion Vulnerability | PAN-SA-2024-0016 | CVE-2024-10231 | 8.8 |
| Prisma Access Browser – ‘Use After Free’ Memory Access Violation | PAN-SA-2024-0016 | CVE-2024-9954 | 8.8 |
| Prisma Access Browser – Input Validation Failure | PAN-SA-2024-0016 | CVE-2024-9965 | 8.8 |
All our vulnerability entries above contain links to official remediation guidance from Palo Alto in the form of their published Security Advisories, as well as details of mitigations or workarounds that can be performed if immediate patching is not possible. Palo Alto networks release free software updates and customers within service contracts are entitled to regular software updates containing security fixes via update channels.
We also recommend scanning your entire estate using the AppCheck vulnerability scanner regularly – both server systems and networking infrastructure, as well as end-user machines running desktop operating systems – in order to detect known vulnerabilities in your technical estate. Contact your account manager now to enquire about license options for our ‘internal scan hubs’ solution or, if not already a customer, take our platform for a test drive today at https://appcheck-ng.com/.
The upcoming dates for the next four monthly PALO ALTO roundups will be:
Add them to your calendar now!
Also keep an eye on our blog for coverage of other critical vulnerability updates including:
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







