OWASP (Online Web Application Security Project) is a non-profit foundation that aims to provide unbiased information and advice surrounding computer and internet application security. They achieve this via operating a number of self-contained projects, each focused on a different remit relating to web application security, from the development of software tools to the running of community events and the creation and publication of training materials.
OWASP are perhaps best known for their flagship “OWASP Top 10 Web Application Security Risks” project, commonly known as the “OWASP Top 10”, which provides a simple risk-based list of the most critical (most common and most impactful) vulnerabilities that should be protected against as a “starter for ten” for those getting started on their cybersecurity journey. However, although it represents a solid, risk-based starting point for smaller businesses, the OWASP Top 10 covers only a tiny fraction of the vulnerabilities that may be present in any given web application. The OWASP foundation also hosts dozens of other projects, many of which provide much more in-depth information and guidance on a broader range of web application security risks, suitable for larger organisations or those operating more critical web application services, and which are listed here

In the areas of security testing and assurance, some major OWASP projects include the OWASP Application Security Verification Standard (ASVS) and OWASP Testing Guide (WSTG), both of which offer very in-depth and detailed scope, technique and methodology guidance aimed at delivering effective web application security testing – that is, testing of web applications to ensure that they do not contain many common types of security vulnerabilities.
However, OWASP found that many of its members and followers (especially financial services companies) required a simpler checklist that represented more comprehensive coverage of vulnerability types than the OWASP Top 10, but yet was more manageable in scope than the ASVS and WSTG projects. Specifically, OWASP recognised the need of many of its members to have access to a simple checklist of best-practice measures for conduct and coverage of penetration testing. The intent of this checklist included its use during RFP (Request For Proposal) or other bidding, onboarding or due diligence assessments of external vendors offering web application security assessment services – specifically in the area of vulnerability scanning and penetration testing.

OWASP therefore developed the OWASP Penetration Testing Checklist as a relatively lightweight set of benchmarks against which vendor offerings could be assessed, focusing primarily on which potential web application security issues should be covered by vendor solutions under best practice.
This list is then published by OWASP
The OWASP Penetration Testing Checklist is aimed at delivering a baseline standard against which potential vendor solutions can be assessed to ensure that a prospective web application security testing provider delivers a service that is sufficient in coverage as well as being both methodical and repeatable in delivery.

As the name suggests, the Penetration Testing Checklist primarily relates as a standard to the delivery of penetration testing (testing performed by a human tester) and not vulnerability scanning solutions such as AppCheck (which are automated). However, there is a large degree of crossover in coverage between the two types of assessment.
Vulnerability scanning and penetration testing are two common forms of cyber security assessment that are conducted to help organisations evaluate, measure and mitigate information security risk and customers are sometimes understandably confused as to what if any differences there are between the two offerings. However, vulnerability scanning and penetration testing are distinct forms of security assessment, and it is important to understand the differences. Vulnerability scanning is an automated form of cyber security assessment that is able to use high-volume machine-driven scanning to discover a very large number of vulnerabilities in a minimal amount of time. Penetration testing, by contrast, is conducted manually by a (human) penetration tester, and often focuses on identifying more complex vulnerabilities that may require human context in order to determine.
AppCheck offers vulnerability scanning services, assessing both web applications and any associated infrastructure such as server and network hardware and equipment.
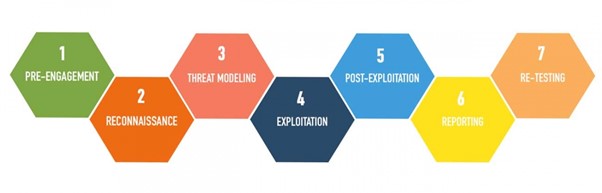
Yes, although the OWASP Penetration Testing Guidelines are primarily published to offer best practice guidance for conducting penetration testing, the coverage in terms of test types performed also aligns well with AppCheck’s sophisticated automated testing methodology based on a “first principles” approach. Unlike more basic vulnerability scanners that may rely purely on conducting checks for “CVEs” (those publicly known cybersecurity vulnerabilities published on publicly available lists and identified based on recognised patterns and software versions), the AppCheck scanner has been developed by experienced penetration testers. The process that the scanner steps through is closely modelled after best-practice penetration testing phases of reconnaissance, threat modelling, vulnerability identification, exploitation and reporting.
AppCheck deliberately does not meet every single recommendation of the OWASP Penetration Testing Checklist, in order to deliver safe and prudent testing that will not impact a customer’s targeted web applications. For example, AppCheck does not perform volumetric testing designed to elicit denial of service (i.e. make the targeted web application unavailable via heavy request loads). Although the OWASP Penetration Testing Checklist recommends performing Application Flooding, AppCheck does not believe that this is a responsible or beneficial form of testing to perform.
For a full comparison of AppCheck features against the OWASP Penetration Testing Checklist, please see our in-depth FAQ article on our helpdesk page
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure.
As always, if you require any more information on this topic or want to see what unexpected vulnerabilities AppCheck can pick up in your website and applications then please get in contact with us: info@localhost.
No software to download or install.
Contact us or call us 0113 887 8380
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network and cloud infrastructure. AppCheck are authorised by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA)







