“Kill chain” is the colloquial name for a concept that originated within the United States military to model the sequential steps that must be conducted in order to successfully plan and deliver an attack and deliver a “kill” (delivery of the objective and destruction of a target). The initial concept of “find, fix, track, target” (FFTT) was first outlined in the late 1990s within official US military doctrine. It was later expanded to “F2T2EA” to explicitly recognise that an attack does not end with the moment when it is initiated but incorporates subsequent phases of ongoing and dynamic engagement and assessment. F2T2EA now constitutes a form of prescriptive and authoritative guidance within US military doctrine under Joint Publication (JP) 3-60, “Joint Targeting” to “provide military guidance for use by the Armed Forces in preparing their appropriate plans…this doctrine will be followed except when, in the judgment of the commander, exceptional circumstances dictate otherwise”. Other similar models used within NATO and other western intelligence agencies and defense forces include “Find, fix, finish, exploit, analyse, disseminate” (F3EAD) and “Decide, detect, deliver, assess” (D3A).
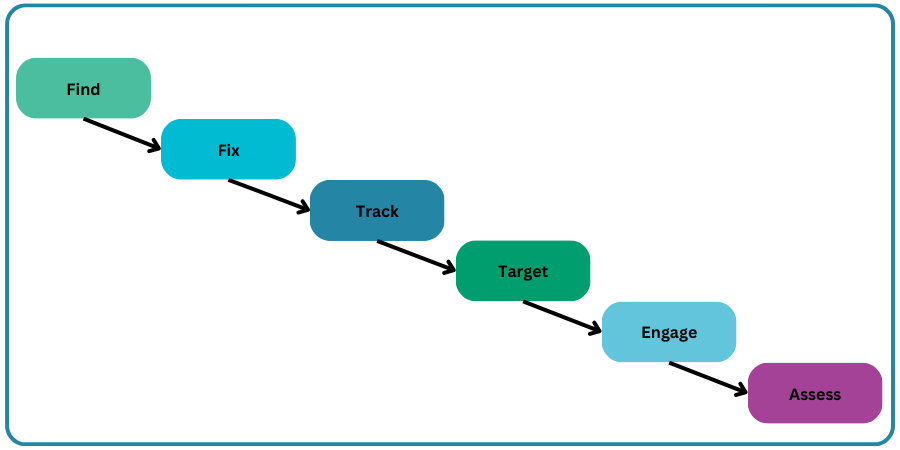
The term “chain” is used in recognition of the fact the models are serial in nature: that is, each phase is considered to be tightly coupled or linked to both the immediately prior and following steps in the sequence, underlying the importance of each phase being delivered upon in turn and without any individual step being skipped or disrupted. The interruption or thwarting of any single “link” in the chain by an adversary is believed to threaten severe interruption that constitutes a serious risk to the ability to successfully prosecute the attack and deliver on the ultimate objective of the attack in question.
Although each kill chain model has a slightly different terminology and number of steps or links in the chain, in general the broad sequence typically includes:
Critically, the model places a great emphasis on the use of intelligence and data assimilation ahead of the engagement. This was originally seen as leveraging new and emerging intelligence capabilities and acting as an enabler for faster response times that deliver greater operational agility.
Cybersecurity, and especially network and web security, is a comparatively new field relative to many other more established sciences, and especially to military doctrine: the Chinese military treatise The Art of War for example famously dates from the fifth century BC! However, it is often possible to draw conceptual parallels between cybersecurity and other, more longstanding domains that can draw on a much longer history of both theoretical research as well as practical application. Consequently, much of the terminology and applied practices of cybersecurity are modelled on concepts from other domains, including the military, such as the principles and concepts of “defense in depth,” “attacks,” “hardening,” “threats,” “penetration,” “attack surfaces,” and “attack vectors.”
With regard to kill chains specifically, the theory is that cyber-attacks, although different in nature to physical attacks, follow a broadly similar pattern of steps during their planning and implementation. By understanding the discrete stages that an attack typically progresses through, it is argued, security teams will have a better chance of identifying attacks and subsequently interrupting or mitigating them before they are carried through to completion.
Because an attack is modelled as a series of chained or sequential phases, awareness of each of the specific phases of an attack prior to the actual triggering or exploitation of the payload can help defenders to “break” the chain of an attempted attack early in its cycle before it can be successfully exploited. A defender’s goal can therefore be seen as understanding the attacker’s actions at each stage, in order to better thwart their intentions.
The “Cyber Kill Chain” concept was first formally published as a model by Lockheed Martin as part of their “Intelligence Driven Defense” methodology. A US security and aerospace company with business units spanning everything from aeronautics to satellites and strategic missiles in addition to cyber defense solutions, Lockheed Martin were perhaps uniquely well placed to translate some of the models and concepts found in traditional warfare and defense communities into the cybersecurity domain.
Translating the military “kill chain” concept to information security, Lockheed Martin promoted the cyber kill chain as a method for modeling intrusions and attacks against a computer network. Whilst in the military field, kill chain models such as F2T2EA are intended to be largely prescriptive (forming a part of formal doctrine regards attack planning), the intention of Lockheed Martin’s Cyber Kill Chain is intended to be primarily descriptive (that is, highlighting to organisations the steps an attacker will take in attempting to compromise their systems). The generic idea of a “cyber kill chain” has subsequently been adopted by many other security organizations to define the typical phases seen during cyberattacks.
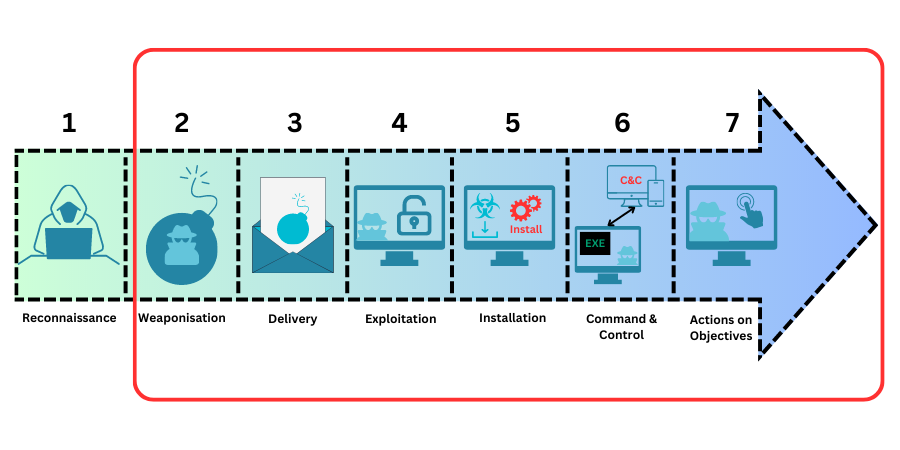
The phases of a cyber-attack outlined within the original Lockheed Martin model are:
As with the military kill chain, Lockheed Martin specifically state that an intruder will succeed in an attack only if they can reach the final stage in the cyber kill chain without being interrupted and blocked by a defender. This means that familiarity with the kill chain offers an inherent advantage to defenders, since they need to successfully mitigate only one phase in the chain, whereas attackers must successfully prosecute every link in the chain in order to deliver on their objectives.
Familiarity with the kill chain model, and awareness of the indicators of compromise associated with each step in the chain can help to grant security teams with early awareness of attempted attacks, in time to head them off. Similarly, familiarity with post-exploit stages that are associated with an ongoing and persistent attacker presence can help teams to identify potential indicators of compromise after the fact and identify persistent threats and past compromises.
Together, this understanding of the broader sequence of an attack both before and after the actual exploit means that security teams are not solely reliant on spotting an attack during the relatively narrow window of its active exploit. The awareness of the pre- and post-exploit phases ensures that security teams have a more holistic view of likely attack patterns and can better identify and protect against attacks in any given phase of their execution.
The kill chain can therefore be leveraged as a management tool within cyber security teams to help teams understand how threats against them may be conducted. With the greater situational awareness this provides, the intention is that teams will be better enabled and prepared for attacks, as well as better informed to improve network defenses intelligently and proactively as a consequence.
Lockheed Martin is the world’s largest defense contractor by revenue and a key contractor to the United States government in particular, supplying according to 2009 records over US $38bn worth of contracts per year. It is perhaps unsurprising therefore that its proprietary cyber kill chain model is explicitly adapted towards defense against what is known as Advanced Persistent Threats (APTs).
An advanced persistent threat (APT) is a threat actor that operates at a highly sophisticated level of technical capability and with significant focus on stealth, seeking to gain unauthorized access to a computer network and remain undetected for an extended period. They often conduct large-scale targeted intrusions for specific goals and have access to sophisticated techniques used in attacks, often creating their own custom malware to exploit previously unknown “0 day” vulnerabilities in targeted systems. The persistent presence means that once a system is compromised, rather than seeking to immediately exploit that system (as a more typical attacker may), the APT is willing to remain dormant and instead leverage the compromised system to pivot further attacks deeper into a target organisation’s network. They are willing to do this because they are not seeking targets of opportunity but rather have a specific mission objective that they need to fulfil, only compromising other systems as needed in order to access a screened system and deliver upon their objective.
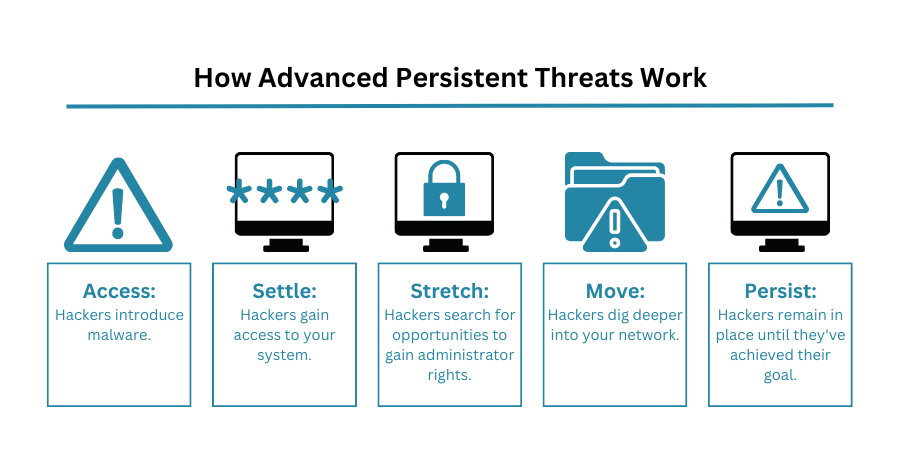
Historically, APTs are typically formed from within nation state intelligence agencies, or state-sponsored groups, with examples including “Cozy Bear” and “Fancy Bear,” both thought to be Russian-backed groups.
This focus on the part of Lockheed Martin is understandable given their customer base but it means that the model may not be as directly applicable in full to all cyber-attacks, especially those that are conducted against smaller businesses, and which may be more opportunistic in nature.
Lockheed Martin’s model of a cyber kill chain is also relatively focused upon modelling attacks that are conducted by external threat actors from outside an organisation’s network perimeter in a classic “outside in” attack. Increasingly porous network infrastructures and insider threats can mean that the model requires some adjustment in order to accurately model these threats.
Many other organisations have attempted to create generic and open-source alternatives to Lockheed Martin’s original Cyber Kill Chain model. These include MITRE’s Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) framework, and the Unified Cyber Kill Chain that was originally produced as a PhD thesis and subsequently published under an open-source licence. There are additionally a proliferation of models that are less generic in nature and attempt to model specific attack scenarios, such as phishing or social engineering attacks.
In general, however, most of the models incorporate steps that involve some form of reconnaissance, followed by the gaining of an initial foothold on a target system or network, and subsequent propagation through the target network as required to deliver on the objectives that the attacker has set.
The idea of “breaking” an opponent’s kill chain is to deploy a control (defense) that can either detect a given attack phase, deny (prevent) the attacker the opportunity to execute a given phase, or to provide a corrective (recovery) option should an attack be successfully conducted. This closely matches the typical grouping of internal cybersecurity controls or defenses into one of three types: preventative, detective, or corrective activities.
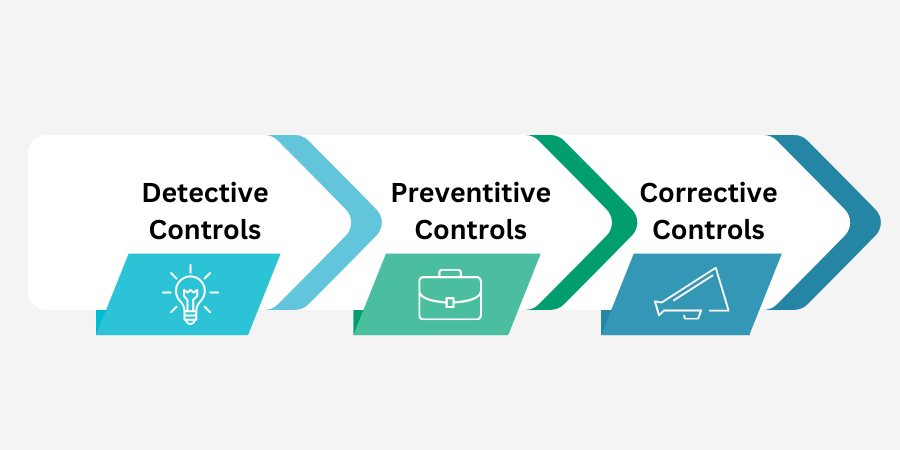
Defensive courses of action can be taken to thwart any of the phases of an attack within the kill chain model:
During the reconnaissance phase, an attacker is performing intelligence gathering against their target. Potential controls against this phase can include the use of threat intelligence platforms to provide intelligence in turn on known threat actors. Platforms such as Digital Shadows are able to alert organisations if stolen credentials or other sensitive or confidential company information is found to become available to attackers on the internet or “dark web.” It is also possible to use web analytics and SIEM (security information and event management) tools to collect data on and provide analytics around website usage, in order to detect unusual access or clusters of unusual activity, such as by building detection alerts for browsing behaviors that are known to be unique to reconnaissance rather than legitimate or typical site access.
Once potential attackers have been identified, it is then possible to take steps to deny them, using either individual-specific blocks on network devices such as firewalls, or by denying certain activity types via measures such as system hardening and web application firewall heuristics.
During the delivery phase, an attacker is aiming to deliver a payload such as malware or a malicious HTML payload to a system. This can be detected via various means that capture and analyze network traffic payloads for malware indicators, including devices such as SSL inspection/offloading and web application firewall (WAF) devices, and network-based (NIDS) or host-based (HIDS) intrusion detection systems.
It is also possible to attempt to thwart the malware or payload installation or activation using system hardening techniques, the use of immutable server platforms, active threat defense and anti-malware or endpoint protection (EPS) system software and reactive firewalls.
During the exploit phase, an attacker is seeking to trigger the payload that they have installed. In some cases, this is inseparable from the delivery phase (above), but in other cases it is a discrete, secondary stage. It can be detected using systems such as endpoint protection (EPS) systems, web application firewalls (WAFs) and SIEM (security information and event management) systems and log analysis.
Regular vulnerability scanning and penetration testing as well as endpoint hardening measures like restricting admin privileges and custom endpoint rules to block shellcode execution can ensure that even if a payload is delivered, it either cannot be executed or cannot be executed in a useful way in that it does not have access to the resources that an attacker desires.
During the C&C phase, an attacker is seeking to leverage their compromise of an initial endpoint in order to either broaden their presence within a target network or establish communications with an attacker’s external command and control infrastructure, so that they can explicitly direct further attacks in a controlled and customised manner based on the target environment and knowledge gained from within the compromised host or system.
Detection as in other steps can be performed using a combination of endpoint protection (EPS) systems, web application firewalls (WAFs) and SIEM (security information and event management) systems and log analysis. Host intrusion detection (HIDS) systems such as Tripwire can provide auditing to discover abnormal file creations and other unauthorised system modifications.
Interfering with the attacker’s command and control of a compromised host or system, however, requires a flexible approach depending on the nature of the host infection. Disruption and containment may involve simply removing a target system’s network connection, so that it is air gapped and can be analysed without it being able to either compromise further systems or “phone home” to an attacker’s external C&C system. Additionally, or alternatively, the attacker’s C&C IP can be blocked explicitly using firewall rules and DLP (data leakage prevention) platforms: this can be done reactively in response to an attack, but also proactively using methods such as IP/DNS reputation blocking, where shared intelligence from other users of a shared security platform can identify attackers even before they target your own systems, allowing you to block them before an attack can be performed.
However, it is important to perform a “damage assessment” in the form of a digital forensic investigation and analysis in order to detect any internal lateral movement of communications after infection so that other infected hosts are found. This is a highly specialised field and will usually require the involvement of subject matter experts such as contracted external consultants in order to be performed.
If an attack has proceeded to this late a phase, then it is also likely that an organisation’s Incident Response Plan (IRP) or incident response “playbook” will have been triggered. This will typically mandate actions including an executive engagement and communications plan, covering any requirements to notify law enforcement and regulatory authorities, as well as customers, investors, and senior management.
It is during the “actions on objective” phase that the attacker finally delivers on their ultimate objective with the attack. Although this will vary depending on the attack type, it may involve data exfiltration or the encryption of data in a ransomware attack, in order to deny its usage to the organisation and disrupt their business continuity until the ransom is paid.
To detect data exfiltration, it is possible to monitor internal network flow as well as data flow outbound across the external network perimeter. However due to the volume of data typically seen, as well as challenges such as data encryption, specialised DLP or Data Leakage Prevention platforms have become available to assist organisation in this regard. Some DLP platforms will integrate with endpoint device security and restrict access to various data at the client and server level.
If a data leak is detected, then some DLP platforms will provide reactive egress filtering in order to disrupt the data exfiltration. Proactive steps can also be taken to ensure that there is appropriate Role Based Access Control (RBAC) and the use of network segmentation and “trust zones” to partition data so that it is at the least risk possible from having the narrowest permitted list of access subjects that does not impair business function.
AppCheck help you with providing assurance in your entire organisation’s security footprint. AppCheck performs comprehensive checks for a massive range of web application vulnerabilities from first principle to detect vulnerabilities in in-house application code. AppCheck vulnerability scanning works by continually attempting to break into and compromise your applications in the same way that a hacker would in order to pinpoint any potential gaps in your security. Our proprietary scanning technology is built and maintained by leading penetration testing experts allowing us to understand how a penetration tester or attacker would explore a given application, allowing it to explore all of your potential weaknesses that a hacker would discover and inform you of how to resolve these before they can be exploited.
AppCheck performs the same “kill chain” steps that an attacker would, combining open-source intelligence gathering and a sophisticated browser-based crawling engine to identify application components that could be vulnerable to attack. The AppCheck crawling engine uses a combination of application modelling techniques and subtle heuristic cues to automatically discover the complete attack surface of any given application in the shortest time possible.
The AppCheck Vulnerability Analysis Engine provides detailed rationale behind each finding including a custom narrative to explain the detection methodology, verbose technical detail, and proof of concept evidence through safe exploitation.
AppCheck is a software security vendor based in the UK, offering a leading security scanning platform that automates the discovery of security flaws within organisations websites, applications, network, and cloud infrastructure. AppCheck are authorized by the Common Vulnerabilities and Exposures (CVE) Program as a CVE Numbering Authority (CNA).
As always, if you require any more information on this topic or want to see what unexpected vulnerabilities AppCheck can pick up in your website and applications then please contact us: info@appcheck-ng.com
No software to download or install.
Contact us or call us 0113 887 8380